This is about java. I would appreciate your help!
Please do not provide a “copy and paste answer”!
Among other things, the purpose of this assignment is to assess the student’s ability to write a program dealing with window events, mouse events, and the Delegation Event Model.
PROGRAM SPECIFICATIONS
Beginning with the file that you downloaded named Proj06.java, create a new file named Proj06Runner.java to meet the specifications given below.
Note that the code in the file named Proj06.java.
Be sure to display your name in both locations in the output as indicated.
When you place both files in the same folder, compile them both, and run the file named Proj06.java, the program must display the text shown below on the command line screen.
I certify that this program is my own work
and is not the work of others. I agree not
to share my solution with others.
Replace this line with your name
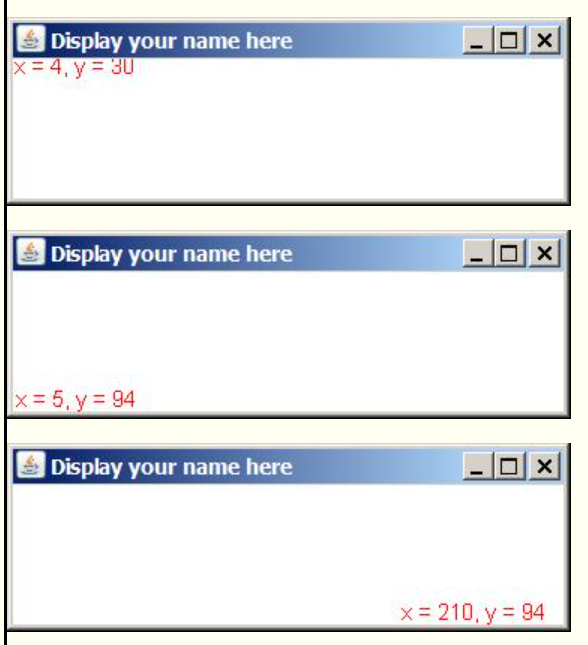
In addition, your program must display a single 300-pixel by 100-pixel Frame object as shown in the images below. When you click the mouse in the working area of the Frame, the coordinates of the mouse pointer must be shown in RED above the mouse pointer. (Multiple images are shown below to show the result of clicking at different locations in the working area of the Frame. Note that the 0,0 coordinate location is at the outer upper-left corner of the Frame, which is beyond the reach of the mouse pointer.)
When you click the X-button in the upper-right corner of the Frame object, the program must terminate and MUST RETURN CONTROL TO THE OPERATING SYSTEM.
You may find it necessary to consult the Java documentation and take class inheritance into account to meet these specifications.
Output:
Proj06.java (can’t be modified)
/*File Proj06
The purpose of this assignment is to assess the student’s
ability to write a program dealing with window events,
mouse events, and the Delegation Event Model.
************************************************************/
// Student must not modify the code in this file.
public class Proj06 {
public static void main(String[] args){
new Proj06Runner();
}//end main
}//end class Proj06
//========================================================//