Complete Exercise questions 1 through 4 found at the end of Chapter 13, CPM 4e. You must select a project that is available online or in print from a news source within 6 months prior to the due date for this assignment. Provide an active link or an image of the source (including date) as evidence and place it as an appendix to your responses to the exercise questions. Use a question-response format for this assignment. Provide in-text citation of all references. Use APA writing style. Turn-it-In will be used to screen this assignment for authenticity. Point allocation will be as follows: Source of project provided and within 6 months prior to the due date for the assignment – PASS/FAIL screen for the assignment. Question 1 – 20 points (ensure that you develop a complete list of as many potential contracted items as possible) Question 2 – 20 points (ensure that you properly cite the reference used to baseline or template your RFI). Question 3 – 20 points (ensure that your ideas are tailored to the project) Question 4 – 20 points (ensure that you explain why the chosen contract is used AND why others were rejected)
Security Architecture
Assessment Description
It is essential as a security expert to be able to evaluate potential risks within the security infrastructure in order to position security controls/countermeasures.
Create an overall security architecture structure diagram with descriptions of the architecture components making sure to:
- Identify all types of data and sensitive data the organization will store.
- Define where that information is stored.
- Record all hardware and software devices in your network.
- Describe how the security controls are positioned and how they relate to the overall systems architecture.
- Define security attacks, mechanisms, and services, and the relationships between these categories.
- Specify when and where to apply security controls.
- Present in-depth security control specifications.
- Address restricting access, layering security, employing authentication, encrypting storage, automating security, and IT infrastructure.
- Include the full scope of policy, procedural, and technical responsibilities.
APA style is not required, but solid academic writing is expected.
Refer to “CYB-690 Security Architecture Scoring Guide,” prior to beginning the assignment to become familiar with the expectations for successful completion.
You are not required to submit this assignment to LopesWrite.
java program to evaluate math expressions using the STACK operations
Write a java program to evaluate math expressions using the STACK operations.
•You must create your own generic stack class. (do NOT use Java built-in Stack class)
Please view the detail in the powerpoint.
Please read the attached document and provide a brief and detailed response to each comments. Please see the attached document for further instructions.
Please read the attached document and provide a brief and detailed response to each comments. Please see the attached document for further instructions.
discussion
does a multilayered defense guarantee that attacks will not be successful? why or why not?
PYTHON
Attached below.
Part 1 is there for now. Part 2 will be available next week.
Assignment
1. Please give in-depth view of Security Threats what are the characteristic of Trojan Horses, Viruses, and Worms. Also brief describe common terms like malware, spyware, bots…etc.
2. Please describe in details what is Denial of Service in terms of common form of Security Attack with example(s).
3. Describe more details then just brief about most common Four-layered Model of Security. Also study/research and brief describe common concepts of whitelisting, blacklisting…etc. in an organization environment.
4.Please read chapter 32 of your textbook and review PP slides and read reputable articles/ web resources and discuss:
How does disaster recovery relate to business continuity? What is the scope of DR? What is the scope of BCP? Please list your reference/s
5.Read chapter 32 , online resources and reputable articles/journals AND:
Choose an organization that you are familiar with, for example a university, place that you are working for or any other organization and write a paper and describe your plan and proposal for a comprehensive Disaster Recovery and Business Continuity plan.
List all your references/resources.
LEED Certification Assessment
Perform a LEED (Leadership in Energy and Environment Design) Certification Assessment of your local living area or work location. Remember to get permission from security. If you wish you may approach the subject in terms of Best Practices.
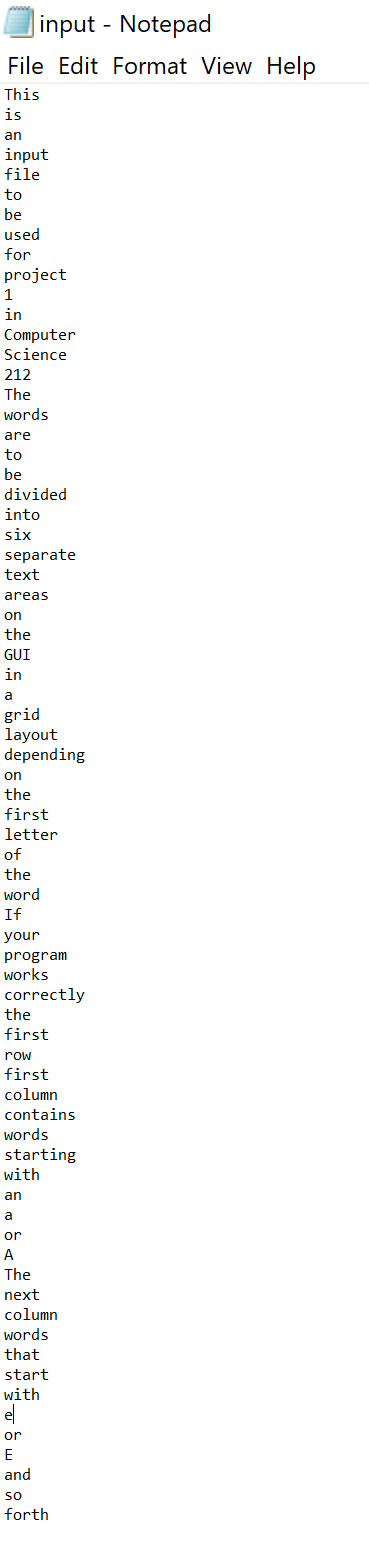
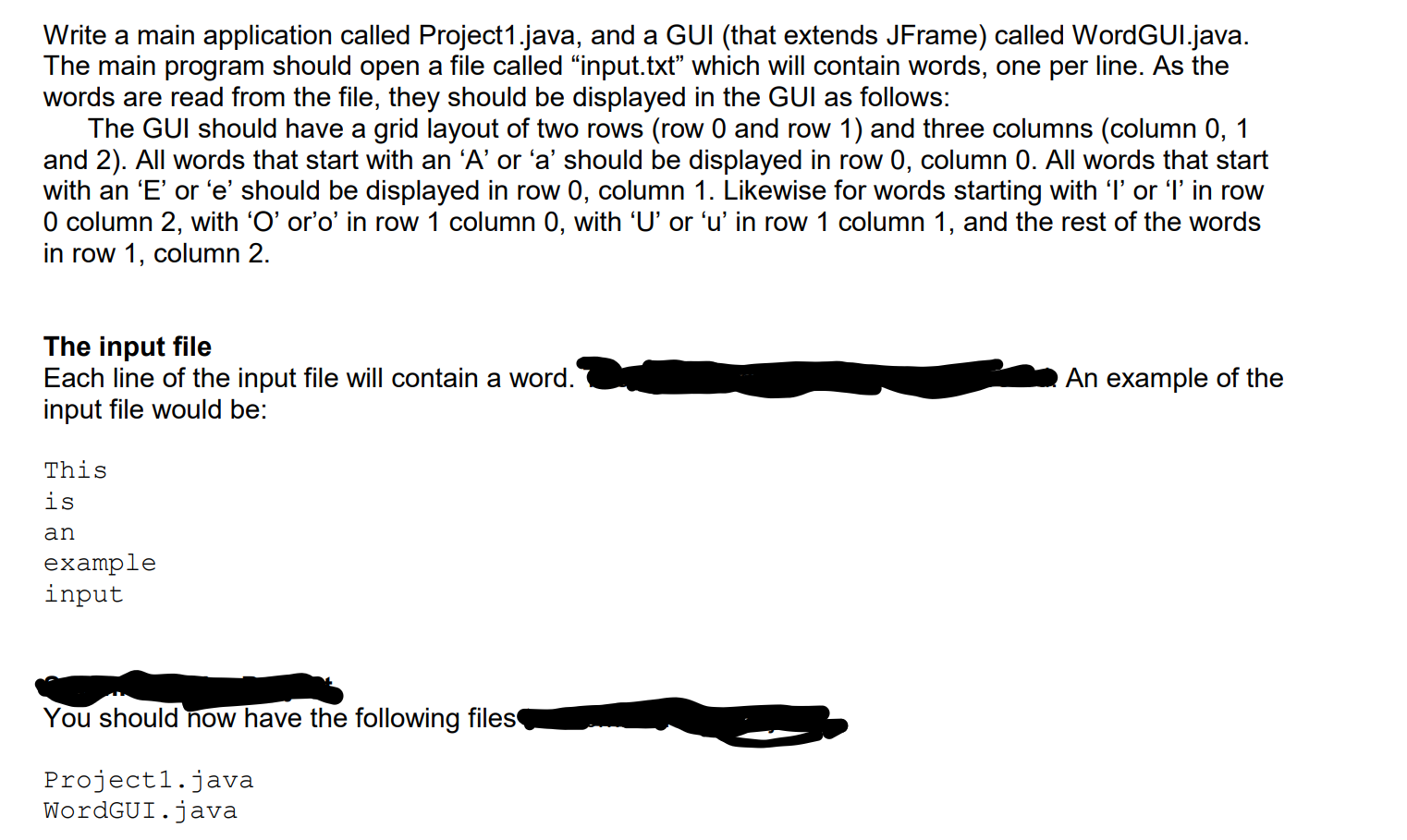
Write a main application called Project1.java, and a GUI (that extends JFrame) called WordGUI.java. The main program should open a file called “input.txt” which
*This is java programming
Write a main application called Project1.java, and a GUI (that extends JFrame) called WordGUI.java. The main program should open a file called “input.txt” which will contain words, one per line. As the words are read from the file, they should be displayed in the GUI as follows:
The GUI should have a grid layout of two rows (row 0 and row 1) and three columns (column 0, 1 and 2). All words that start with an ‘A’ or ‘a’ should be displayed in row 0, column 0. All words that start with an ‘E’ or ‘e’ should be displayed in row 0, column 1. Likewise for words starting with ‘I’ or ‘I’ in row 0 column 2, with ‘O’ or’o’ in row 1 column 0, with ‘U’ or ‘u’ in row 1 column 1, and the rest of the words in row 1, column 2.
“input.txt” file is looks like that:
Activity 6- Project HR & Stakeholder Mngt
How does communicating with stakeholders virtually versus in-person differ? Is one more effective than another?
Text
Title: Managing Project Stakeholders
ISBN: 9781118504277
Authors: Tres Roeder
Publisher: John Wiley & Sons
Publication Date: 2013-04-22