- Describe DBLC (Database Life Cycle) and its phases.
- Describe concurrency in a DBMS and how it is managed.
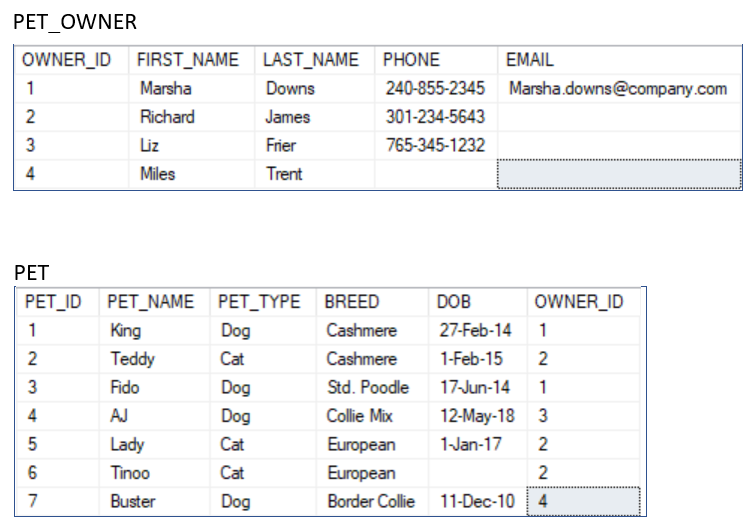
For the following tables write the required SQL statements:
3. Write an SQL statement to create the PET table.
4. Write an SQL statement to show the breed and type of all pets.
5. Write an SQL statement to display the breed, type, and DOB of all pets having the type Dog.
6. Write an SQL statement to show the pet owner first name, last name, and pet name. Hint: you need to link PET_OWNER and PET tables.
project:
A factory has several departments. A department may have many employees but must have at least seven. Every employee works for one and only one department. Every department has a manager — only one manager per department. A manager is an employee of the company, but not all employees are managers. A department may have many machines, and every machine is assigned to a specific department. Products are produced on machines. A product can be an assembly of several different components or a single piece. Every product goes through one or more machines for appropriate production operations. Likewise, several products may go through a particular machine for a production operation. The employee has a first name, last name, and middle name, gender, address, and salary. An employee number uniquely identifies an employee. Departments have departments name, type, and location. The department’s name and number are both unique identifier of a department. Every machine will have a unique machine number, name, type, and vendor’s name.
When a machine goes for maintenance, the date of maintenance must be captured, since a maintenance activity is identified by the date of the maintenance for each machine. The attributes of maintenance activity are time taken and cost.
A product is identified by its component ID, component name, and description.
7- Create an ERD by first identifying the entities, then their relationships, and finally add the attributes to each entity.
8- Create a logical data model from ERD, including primary and foreign keys.
9- Implement the logical model into a DDL and build the database in SQL Server (or any other DBMS that you have installed)
10- Create some synthetic data and insert the data into the database.
