In 250 words
Use the Web to search for methods to prevent XSS attacks.
Write a brief description of more than one method
In 250 words
Use the Web to search for methods to prevent XSS attacks.
Write a brief description of more than one method
Submit a one-page outline with your proposed term paper title, thesis statement, and an outline of the subtopics you will cover in your paper. You may choose any computer-related crime. When choosing a specific computer crime, make sure that you are able to find relevant cases to support your topic. ALL TOPICS MUST BE APPROVED BY SUBMISSION IN WEEK 1!
Include at least 3 references supporting your paper research.
Complete all the tasks with Jupyter Notebook.
Submit your notebook
Given the relational model below, using your ADU ID and SQL statements.
List all your courses of the last term [0.5 pt.]
List the instructors’ names of these courses in descending order [0.5 pt.]
List all courses of the last term that have no prerequisite [0.5 pt.]
List all courses of the last term with grade above ‘C’ [0.5 pt.]
Determine the CSIT department of the last term courses [1 pt.]
Define the courses of the last term that have more than one section [1 pt.]
Display the sections of the courses above that are offered in your location (‘Abu Dhabi’ or ‘Al-Ain’) [1 pt.]
Please attach your last semester schedule details for crosschecking.
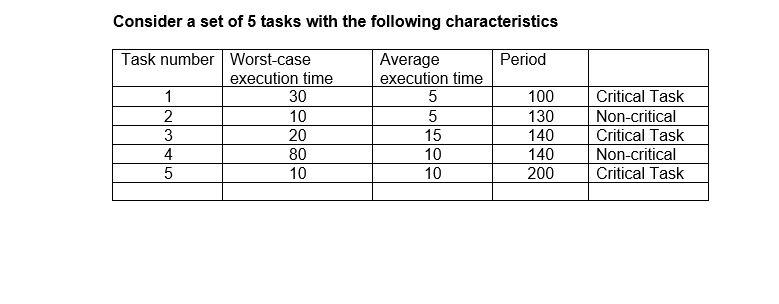
1. Write a 2-3 page paper where you compare and contrast the differences between Identity as a Service, Infrastructure as a Service and Identity Access Management. The submission needs to include a minimal of 3 scholarly resources in APA format.
2. Define and describe Platform as a Service. In the description be sure to list the benefits and potential disadvantages. Locate an article that supports the benefits of PaaS in an organization and/or the failures of PaaS implementation. Be sure to cite in APA format.
No plagiarism
Objective
● list and string handling: split, indexing, len()
● list comprehension, with if and else
● if statement
● file reading, csv file handling (csv: comma separated values)
● nan: not a number. matplotlib will auto ignore all ‘nan’ entries.
● matplotlib: make line plots, line/dot style, label, saving figure
● self learning. (google and follow example)
For this assignment research and discuss the various security related components that must be addressed when implementing any system (HINT: the first is policy). Include citations and sources in APA style.
500 words.
Topic – Spam Email Detection
Research content (at least 1000 words and 6 references – 3 must be scholarly peer-reviewed articles)
Create visualizations using R Language as applicable, discuss findings
**Must be APA formatted** **College Level Writing****No grammar issues and no spelling issues**
In this individual assignment, you will perform an exploratory analysis with What-If Tool, to better understand the structure of datasets, investigate initial questions, and develop preliminary insights and hypotheses. Your final submission will take the form of a report consisting of key insights gained during your analysis.
Pick two datasets. These can be ones that are available for demo at https://pair-code.github.io/what-if-tool/explore/ (Links to an external site.). But we’ll give you additional points if you choose to use datasets that are not available there.
After selecting datasets – but prior to analysis – write down an initial set of three questions you’d like to investigate about the datasets and prediction results from ML models.
Next, you will perform an exploratory analysis of your dataset and results from ML models using What-If Tool. You can either use their web demo if you use their provided datasets. You can also use notebooks and revise them with your datasets and models.
You should consider two different phases of exploration.
In the first phase, you should seek to gain an overview of the structure of your datasets and results from their models. What is the structure of datasets? Which features are used? Are there any notable issues with the distributions of datasets? What is the model performance? What features contributed the most? Are there any surprising relationships among subsets of data and model results? Are there any fairness issues?
In the second phase, you should investigate your initial questions, as well as any new questions that arise during your exploration. For each question, playing with the visualizations in What-If Tool, that might provide a useful answer. Interact with their functionalities (e.g., datapoint editors, dropdown menus, fairness analysis) to develop better perspectives, explore unexpected observations, or sanity check your assumptions. You should repeat this process for each of your questions, and also feel free to revise your questions or branch off to explore new questions.
You’ll submit a single PDF as a form of a report. For each dataset, you will provide 10 most interesting or surprising findings (or “insights”) with details and screenshots. Your “insights” can include important surprises or issues (such as skewed data distributions, critical fairness issues) as well as responses to your analysis questions. Each finding will consist of a title and 2-4 sentence descriptions, and screenshots. Provide sufficient detail so that anyone could read through your report and understand what you’ve learned. You are free, but not required, to annotate your images to draw attention to specific features of the data.
Do not submit a report cluttered with everything little thing you tried. Submit a clean, succinct report that highlights the most interesting, insightful observations. You don’t need to tell us how the tool works — we already know that. Think of this like a report to your manager who wants to know what the datasets look like and how the model worked.
The structure of the report will be:
Grading