Please write 350 words essay on the above.
Project Assignment
Write a 6-8 page paper (deliverable length does not include the title and reference pages)
- What are the principles and limitations to an individual’s right to privacy?
- What are the trade offs between security and privacy?
- What is the issue of freedom of speech versus the protection of children online?
Due: Assignment is due on the day stated in the Course Schedule
- Provide three articles to substantiate the above three questions.
- Use APA format to provide a citation for each of the articles you read.
- Suggestion: Use a search engine (Google) and keywords.
Easy Cyber questions
1. Distinguish between vulnerability, threat, and control.
2. Theft usually results in some kind of harm. For example, if someone steals your car, you may suffer financial loss, inconvenience (by losing your mode of transportation), and emotional upset (because of invasion of your personal property and space). List three kinds of harm a company might experience from theft of computer equipment.
3. List at least three kinds of harm a company could experience from electronic espionage or unauthorized viewing of confidential company materials.
4. List at least three kinds of damage a company could suffer when the integrity of a program or company data is compromised.
5. List at least three kinds of harm a company could encounter from loss of service, that is, failure of availability. List the product or capability to which access is lost, and explain how this loss hurts the company.
6. Describe a situation in which you have experienced harm as a consequence of a failure of computer security. Was the failure malicious or not? Did the attack target you specifically or was it general and you were the unfortunate victim?
7. Describe two examples of vulnerabilities in automobiles for which auto manufacturers have instituted controls. Tell why you think these controls are effective, somewhat effective, or ineffective.
8. One control against accidental software deletion is to save all old versions of a program. Of course, this control is prohibitively expensive in terms of cost of storage. Suggest a less costly control against accidental software deletion. Is your control effective against all possible causes of software deletion? If not, what threats does it not cover?
9. On your personal computer, who can install programs? Who can change operating system data? Who can replace portions of the operating system? Can any of these actions be performed remotely?
10. Suppose a program to print paychecks secretly leaks a list of names of employees earning more than a certain amount each month. What controls could be instituted to limit the vulnerability of this leakage?
Phd Interview Questions
WRITTEN INTERVIEW QUESTIONS
DOCTORAL CANDIDATES SHOULD PROVIDE AN AUTHENTIC PERSONAL STATEMENT TO EACH OF THE FIVE FOLLOWING QUESTIONS/PROMPTS REFLECTING ON THEIR INTERESTS. IN THE EVENT THAT ANY OUTSIDE RESOURCES ARE USED, RESOURCES SHOULD BE CITED IN APA FORMAT. SUBMISSIONS SHOULD BE A MAXIMUM OF 500 WORDS OR 125 WORDS PER QUESTION/PROMPT. IT IS BEST TO RESPOND TO EACH PROMPT/QUESTION INDIVIDUALLY FOR CLARITY OF THE REVIEWER. WRITING SAMPLES SHOULD BE SUBMITTED IN MICROSOFT WORD FORMAT AND INCLUDE THE CANDIDATE’S NAME.
1. PROVIDE A BRIEF INTRODUCTION FOCUSING ON YOUR EDUCATION, CAREER, AND DECISION TO APPLY TO UNIVERSITY OF THE CUMBERLANDS.
2. IN RELATION TO YOUR DOCTORAL PROGRAM APPLICATION, WHAT AREA OF RECENT RESEARCH IN THE FIELD WOULD YOU WANT TO STUDY, AND WHY?
3. HOW DOES YOUR CURRENT VOCATION RELATE TO YOUR APPLICATION TO THE DOCTORAL PROGRAM?
4. HOW WILL YOUR EXPERIENCES AND PERSONAL SKILLS HELP YOU TO BE SUCCESSFUL IN YOUR PROGRAM?
5. WHAT LONG-TERM GOALS DO YOU HAVE FOR APPLYING YOUR LEARNING FROM YOUR DOCTORAL PROGRAM?
Computer Science Homework
Please read the whole instructions and solve without the use of arrays, functions, pointers, references, and any other usual concepts.
Week 4 Research Paper – Info Tech Import Strat Plan
This week, you have read about server virtualization and cloud computing in chapter 6 of your textbook. For your written assignment this week, complete a case study of the organization you work for (use a hypothetical or “other” organization if more applicable) that will address the following prompts:
• Describe the organization’s environment, and evaluate its preparedness for virtualization.
• Explain Microsoft (or another product) licensing for virtualized environments.
• Recommend a configuration for shared storage; make sure to discuss the need for high availability and redundancy for virtualization for the organization.
• Explain Windows Azure capabilities for virtual machines and managing a hybrid cloud, including Windows Azure’s Internet as a Service (IaaS) and storage capabilities
Make a recommendation for cloud computer use in the organization, including a justification for your recommendations.
Submit your midterm research paper as a single document. Your paper should meet the following requirements:
• Be approximately four to six pages in length (1200-1800 words), not including the required cover page and reference page.
• Follow APA7 guidelines. Your paper should include an introduction, a body with fully developed content, and a conclusion.
• Support your answers with the readings from the course and at least two scholarly journal articles to support your positions, claims, and observations, in addition to your textbook. The UC Library is a great place to find resources.
• Be clearly and well-written, concise, and logical, using excellent grammar and style techniques. You are being graded in part on the quality of your writing.
ITSD324:Project Testing and Software Quality Assurance
Assignment Description
Automation testing is an important task that will help you reduce the time it takes to execute a test case. In this assignment, you will install a trial version of an automation testing tool and then create automation test cases.
The automation testing process includes the following stages:
- Select the appropriate tool.
- Determine the test cases that should be automated.
- Implement the automated test cases.
- Record the test script.
- Save the test script.
- Execute and analyze the test results.
Please follow the step-by-step instructions and screenshots below to install the tool (Micro Focus, 2018):
- Step 1: Use the search engine, and search for Unified Functional Testing Trial Version.
- Step 2: The browser will take you to the Microfocus site.
- Step 3: Enter all details and click “Free Trial.”
- Step 4: Go to “All Products,” and click the UFT Download button.

- Step 5: Click on the UFT Version_SetUp.exe file.
- Step 6: It will take at least 10 minutes to download the .exe file.
- Step 7: Click on the .exe file.
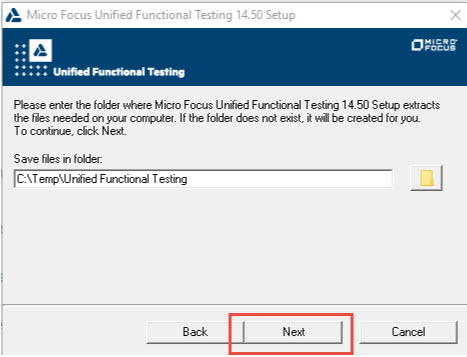
- Step 8: Verify the path, and click “Next.”
- Step 9: Click “Next.”
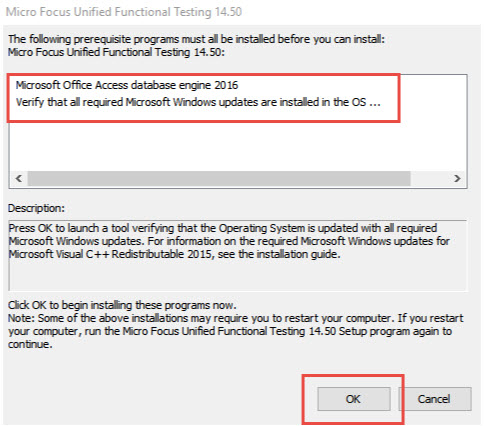
- Step 10: Verify all of the prerequisites, and continue with installation.
- Step 11: Click the Next button.
- Step 12: Select “I accept the terms” in the License Agreement, and click “Next.”
- Step 13: Select all of the add-ins, and click “Next.”
- Step 14: Click “Next.”
- Step 15: Click “Install.”
You can also use this PDF file for installation help.
- Step 16: Once the installation is complete, open the tool and create the sample test.
- Step 17: Follow this URL, and learn how to create an automated test for the Sample MyFlight application.
- Step 18: You can use either the Calculator application from Unit 2 or the sample MyFlight application to create additional automated test cases.
- Calculator application: Calculator executable file and source code file.
You need to create at least 4–5 automation test cases using either Sample MyFlight or the Calculator application.
Submit the following in a .zip file:
- Output screenshot of UFT installation
- Entire solution folder that contains 4–5 automation test cases
Dynamic Programming
I have fundamentally grasped the concept of DP but i am struggling to apply this to this context
Discussion
A simulated disaster and comprehensive recovery test may involve many of an organization’s key personnel for several days: is this a reasonable burden to place on a busy, competitive company? How would you argue against the inevitable tendency to shortcut the procedure
cs
Purpose
This discussion activity gives you the opportunity to solve a real world scenario. In doing so, you will learn the concepts of a software development cycle.
Directions
Part I: Complete Your Original Response to the Main Topic
You are a software developer for a Retail Point of Sale System Company. A client has made a request to upgrade the current system from command line interface to a graphic user interface. The client concerns on an effect to the current system with the change. The client does not want to lose any current data on the system. Provide recommendations and the change plan including the below requirements to the customer.
Requirements:
- Create a requirement plan (what need to be done to support this upgrade)
- Create a development plan (how to implement this upgrade with programming details explanation including technical details on this document)
- Create testing plan (how to ensure that the new upgrade works without affecting current system and no data lost.)
Posting your recommendations and the change plan
Once you have completed your recommendations and plan. Post it in the discussion forum by clicking the Reply link below.
- In the first line of your post, your should add your plan title and name.
- Your posting must include recommendations, a requirement plan, a development plan, and a testing plan.
