*This is java programming
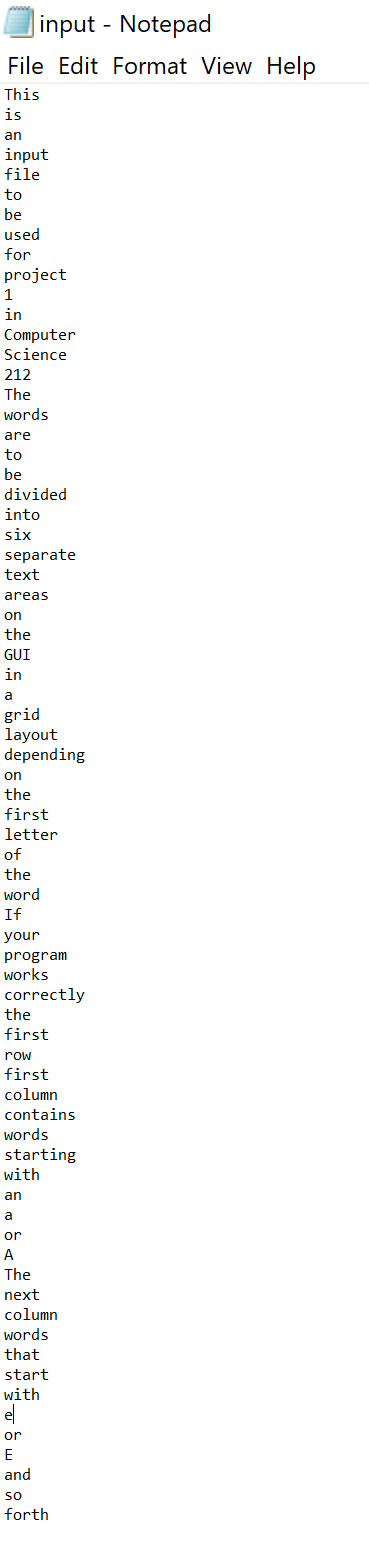
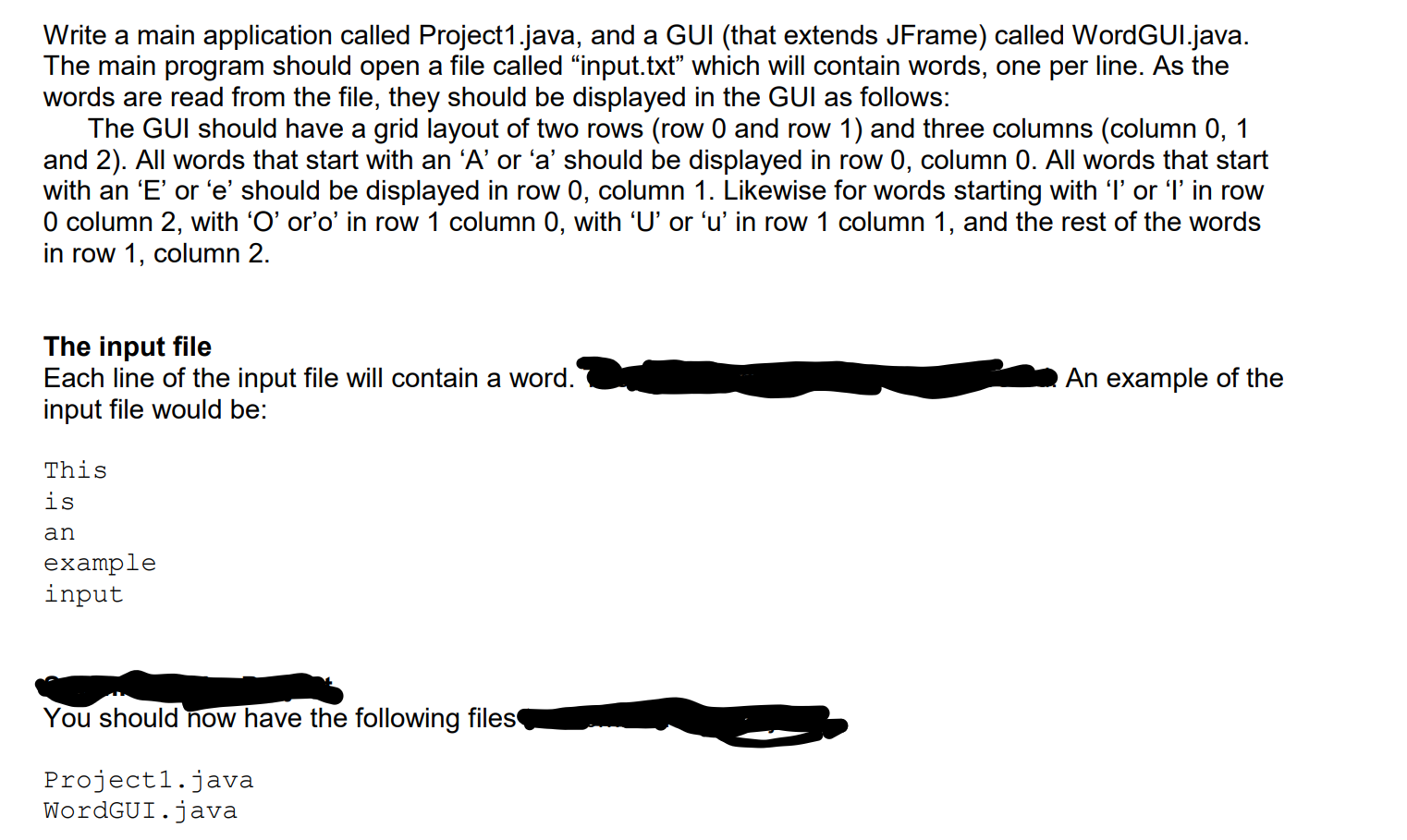
Write a main application called Project1.java, and a GUI (that extends JFrame) called WordGUI.java. The main program should open a file called “input.txt” which will contain words, one per line. As the words are read from the file, they should be displayed in the GUI as follows:
The GUI should have a grid layout of two rows (row 0 and row 1) and three columns (column 0, 1 and 2). All words that start with an ‘A’ or ‘a’ should be displayed in row 0, column 0. All words that start with an ‘E’ or ‘e’ should be displayed in row 0, column 1. Likewise for words starting with ‘I’ or ‘I’ in row 0 column 2, with ‘O’ or’o’ in row 1 column 0, with ‘U’ or ‘u’ in row 1 column 1, and the rest of the words in row 1, column 2.
“input.txt” file is looks like that: